Office 365 Hardening
Increase the robustness of your Office 365 security to deter criminals.
4 stages of Office 365 Hardening
Office365 Tenant Review
Office365 tenant hardening
Office365 follow-up periodic tenant review
Office365 active monitoring and alerting service
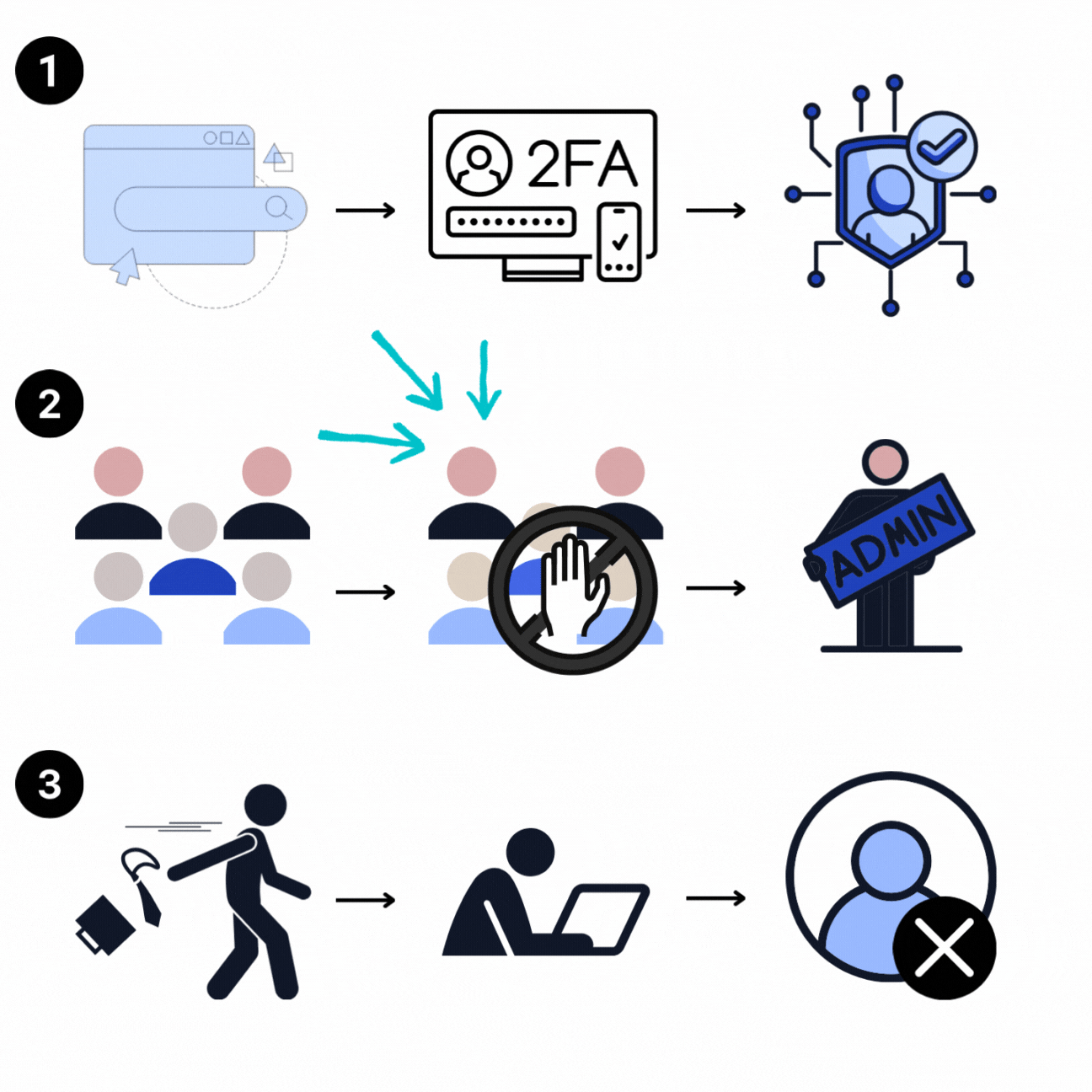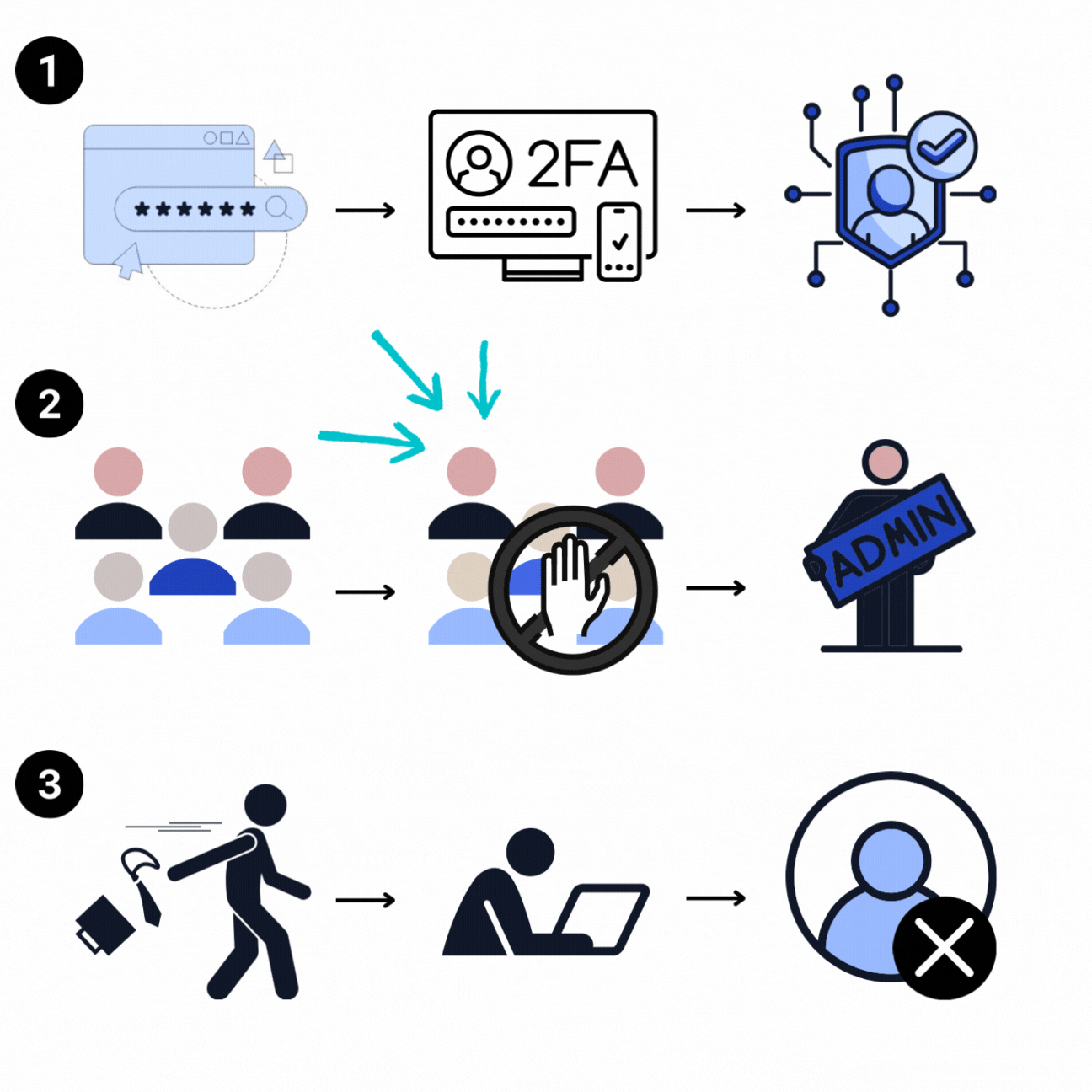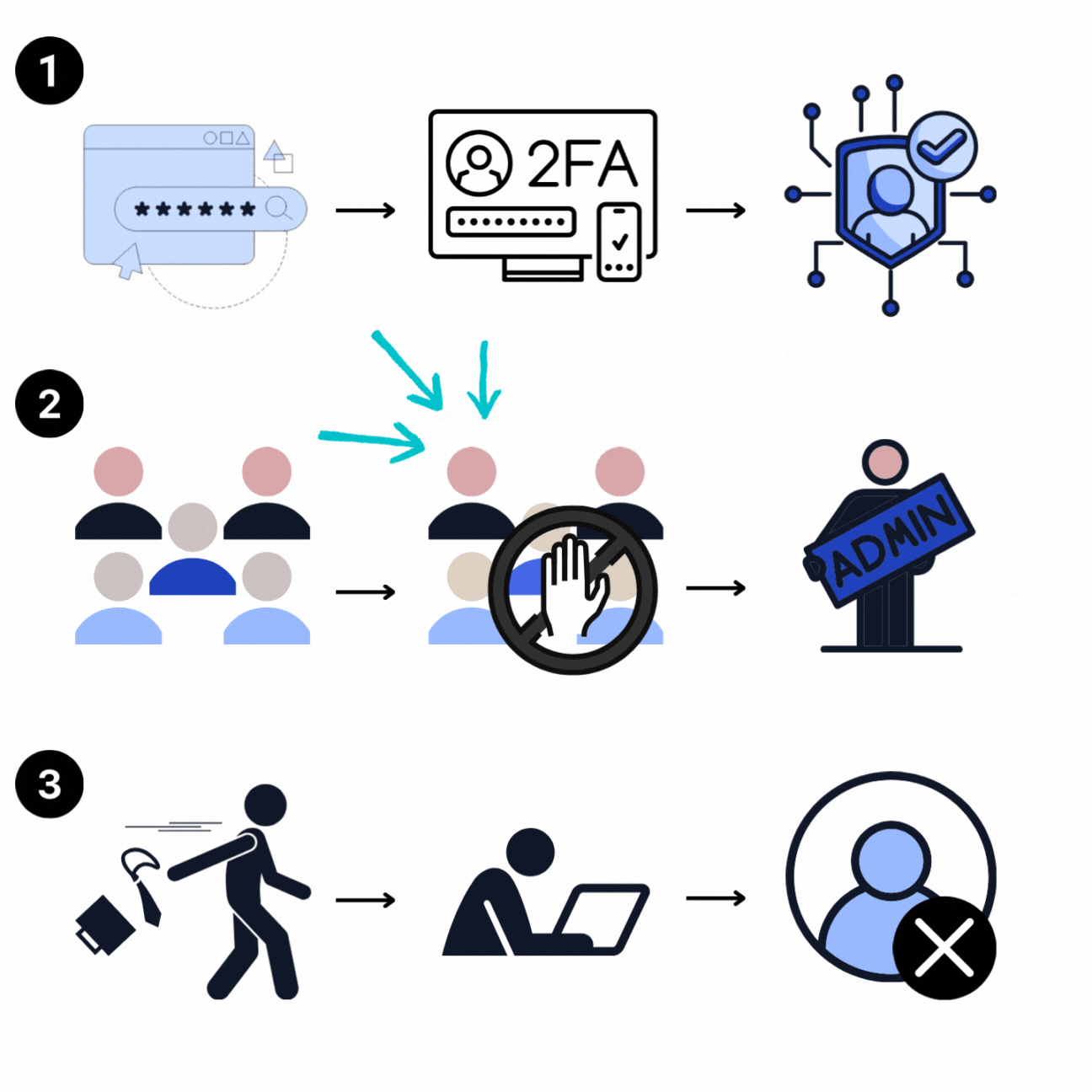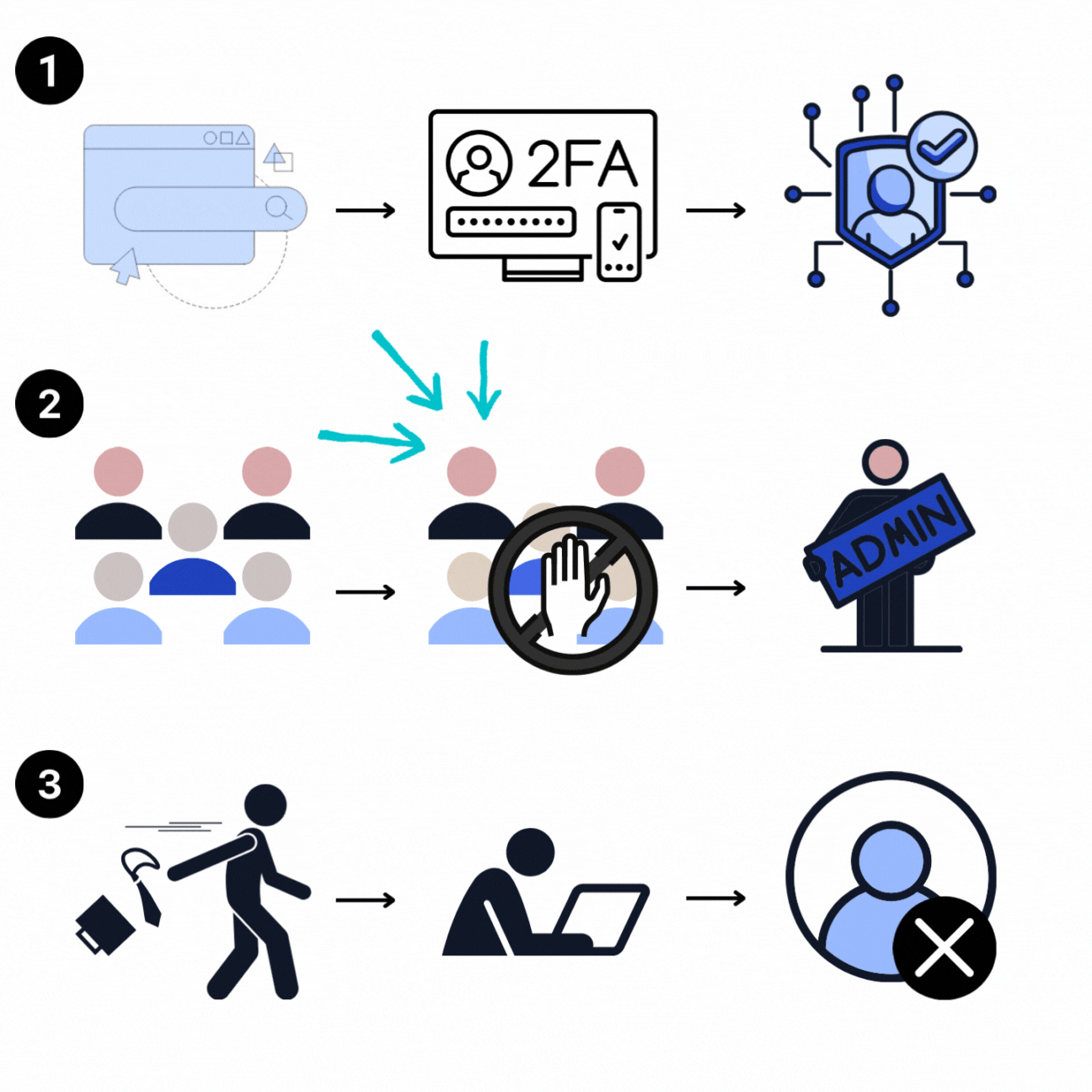
Office365 Tenant Review
This is an initial assessment of the current state of your cloud email system. A few areas we will review:
- Email system (also known as exchange online)
- Microsoft Teams permissions and apps
- OneDrive permissions
- SharePoint permissions and apps
- AzureAD, global permissions, and apps
- Conditional access and multi-factor authentication (MFA)
After the review is completed, you will receive a report detailing steps to take to enhance your email reputation and improve your Office365 tenant security.
Office365 Tenant Hardening
Following the tenant review we can implement some or all the recommended actions on your behalf.
- Setup tenant MFA with the Microsoft authenticator app
- Protect your organization reputation with domain security
- Remove and reconfigure resource access.
- Deploy conditional access
- Deploy tenant backup
- Deploy spam and malicious email protection
After the review is completed, you will receive a report detailing steps to take to enhance your email reputation and improve your Office365 tenant security.


Office365 follow-up periodic tenant review
To keep up with the latest security trends, we conduct a follow-up review every 60 to 90 days.
Office365 active monitoring and alerting service
For larger environments periodic reviews are not enough. To satisfy the security and compliancy needs in these environments, we partnered with some industries leaders to develop a set of automation tools that can be deployed in either a co-managed or a fully managed service.
With this service your business will :
-
Receive reports on login failures (triggered by MFA or conditional access) - Receive notifications when user privilege changes.
- Receive notifications of suspected unauthorized activity